Version 8.3.7 of the Sendio software gives admins the ability to configure LDAPS in Directory configuration. Previously, assistance from Sendio Support was required in order to enable LDAPS on a Sendio instance.
Microsoft has recently advised customers to enable LDAP channel binding and LDAP signing to prevent man-in-the-middle attacks. Making these changes to Active Directory requires all LDAP clients to use LDAPS.
When the advisory was initially released in August of 2019 Microsoft stated that the March 2020 update would force LDAP channel binding and LDAP signing. On March 10, 2020 Microsoft revised their advisory and stated that the change to force LDAP channel binding and LDAP signing would not happen with the March 2020 update nor would it be applied in an update in the foreseeable future.
Although this change to force LDAPS is not being forced we do still recommend updating your Sendio configuration to connect to your Active Directory via LDAPS.
Preparation steps:
1. Enable LDAPS in the Active Directory Domain Controller your Sendio synchronizes to.
2. Create a firewall rule to allow access to either port 636 or port 3269 on your Domain Controller.
Sendio LDAPS configuration steps:
1. Login to the Web UI as an Admin
2. In the Directories tab select the Directory you would like to enable with LDAPS
3. Select “Use ldaps”
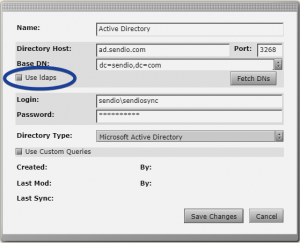
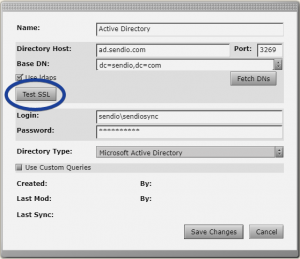
After selecting the “Use ldaps” checkbox, a “Test SSL” button will appear and will allow validation of your LDAPS connection to your Active Directory.
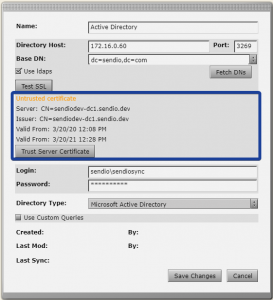
If you’ve configured a self-signed certificate on your Active Directory you’ll have the opportunity to Trust the self-signed certificate.